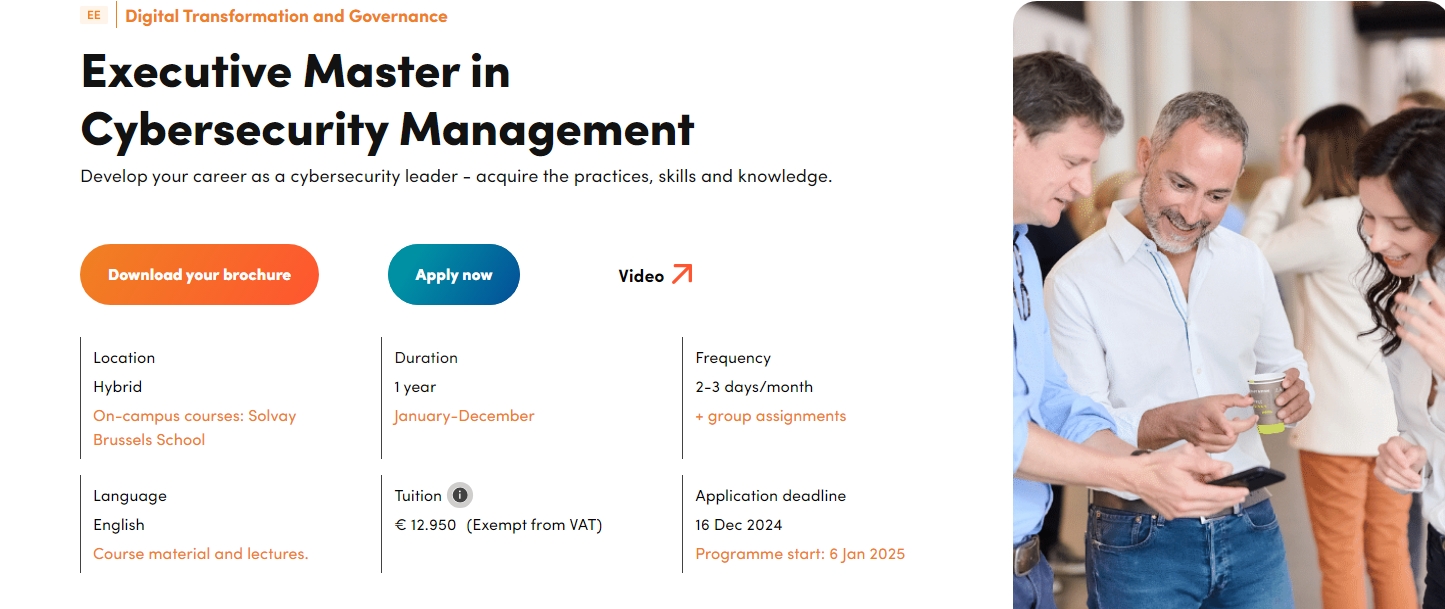
Cyber Education for executives and board members
As required by NIS2 Directive and country laws.
Board Education on Cybersecurity as required by NIS2 Directive and country laws.
Bring leadership to executives on cybersecurity decision making. Catch-up with essentials and embark with those who have the know-how.
Short education series for Board and executives with four sessions of two hours.
Participants receive an attendance certificate.
Join open sessions or request your own in-company session.
NIS 2 - Article 20 – Governance
1. Member States shall ensure that the management bodies of essential and important entities approve the cybersecurity risk-management measures taken by those entities to comply with Article 21, oversee its implementation and can be held liable for infringements by the entities of that Article. The application of this paragraph shall be without prejudice to national law as regards the liability rules applicable to public institutions, as well as the liability of public servants and elected or appointed officials.
2. Member States shall ensure that the members of the management bodies of essential and important entities are required to follow training, and shall encourage essential and important entities to offer similar training to their employees on a regular basis, in order that they gain sufficient knowledge and skills to enable them to identify risks and assess cybersecurity risk-management practices and their impact on the services provided by the entity.


DORA - Article 5 – Governance and Organization
1. Financial entities shall have in place an internal governance and control framework that ensures an effective and prudent management of ICT risk, in accordance with Article 6 in order to achieve a high level of digital operational resilience.
2. The management body of the financial entity shall define, approve, oversee and be responsible for the implementation of all arrangements related to the ICT risk management framework referred to in Article 6.
3. Financial entities, other than microenterprises, shall establish a role in order to monitor the arrangements concluded with ICT third-party service providers on the use of ICT services, or shall designate a member of senior management as responsible for overseeing the related risk exposure and relevant documentation.
4. Members of the management body of the financial entity shall actively keep up to date with sufficient knowledge and skills to understand and assess ICT risk and its impact on the operations of the financial entity, including by following specific training on a regular basis, commensurate to the ICT risk being managed.